Information Security Management and Accreditations
Information Security Promotion Organization
Kaohsiung Chang Gung Memorial Hospital was approved by the Executive Yuan on January 30, 2020, and its information security responsibility level is a Class A specific non-public agency.
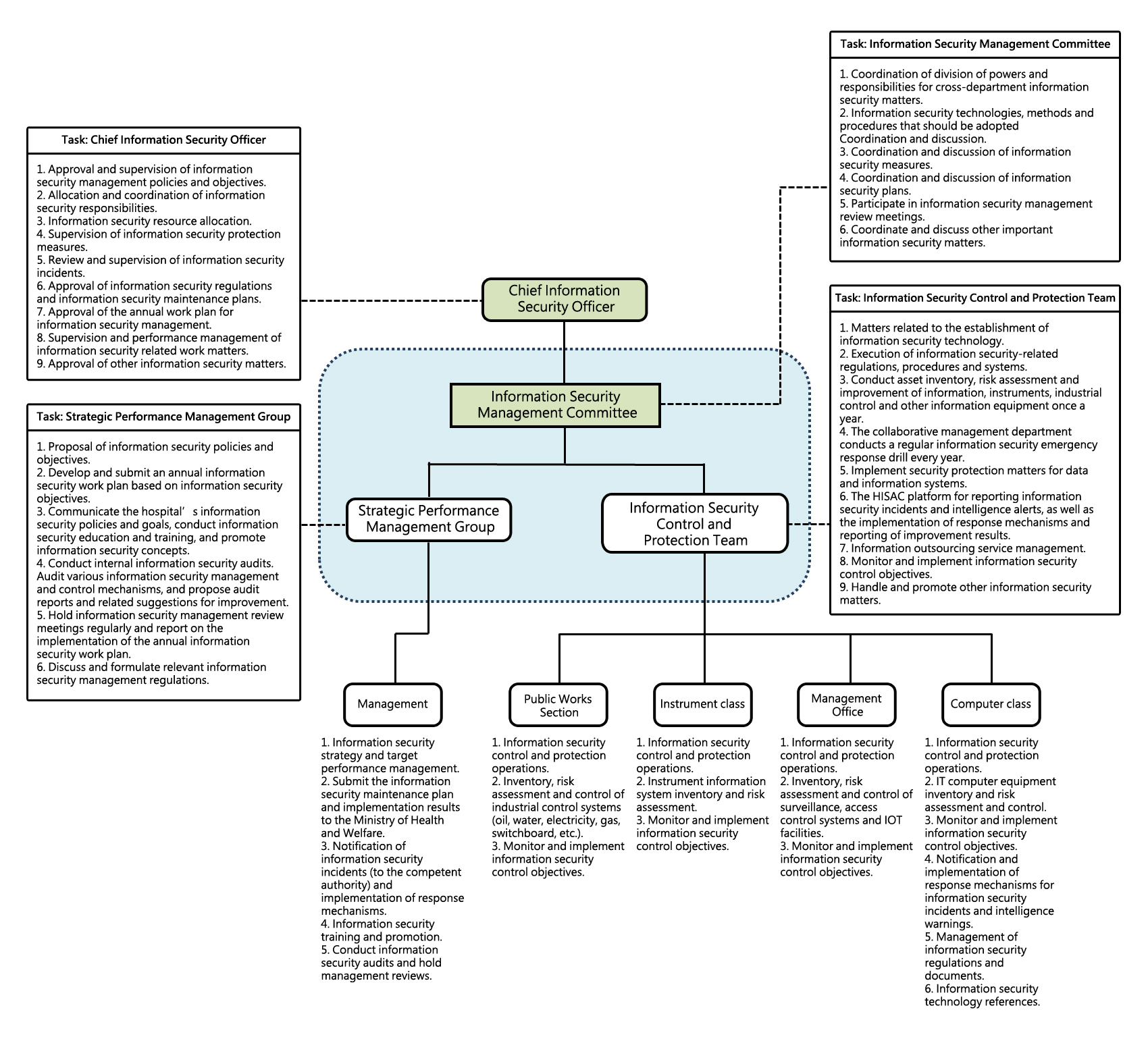
The Information and Communications Security Committee is affiliated to the Academic Affairs Committee and has a strategic performance management group, which is mainly implemented by the Management Department in policy formulation, promotion and education and training; the Information Security Control and Protection Group includes computer classes, instrumentation, management offices, public works offices, etc. IOT risk assessment and inventory, abnormal response and other operations
Information Security Policy
In order to ensure the smooth operation of the hospital's business, prevent information or communication systems from unauthorized access, use, control, leakage, destruction, tampering, destruction or other infringements, and ensure their Confidentiality, Integrity and Availability for all colleagues to follow:
- Establish an information security risk management mechanism to regularly review the effectiveness of information security risk management in response to changes in internal and external information security situations.
- Protect the confidentiality and integrity of smart information systems and information from unauthorized access and tampering.
- Strengthen the resilience of the IT system to ensure business continuity.
- Each department should cooperate with the hospital's information security policy to conduct asset inventory, risk assessment and information security protection response.
- In response to changes in the information security threat situation, handle Information security education and training, in order to improve the information security awareness of our colleagues, colleagues should also participate in the training.
- Rewards should be given to those who have made meritorious service in handling information security business.
- Do not open emails from unknown sources or from which the sender cannot be clearly identified.
- It is prohibited for multiple people to share a single information system account.
The information security policy ensures the confidentiality, integrity, and availability of information to avoid infringement. Last year, three information security courses were held to increase information security awareness.
Information security goals
Quantitative goals
- Maintain information system Continue to operate stably.
- Confidentiality: information omission, tampering and data leakage incidents, The number of times per month is zero.
- Integrity: Cases of unauthorized alteration or destruction of data, The number of pieces per month is zero.
- Confirm that 100% notification of information security incidents will be completed within 1 hour, and 100% completion of the case will be completed in accordance with the time limit specified by the classification of information security incidents.
- The attachment opening rate and link click rate of the email social engineering exercise were less than 9.4% and 3.8% respectively.
Qualitative goals
- Timely adjust the content of information security maintenance in response to changes in laws and technology to prevent information systems or information from unauthorized access, use, control, leakage, damage, tampering, destruction or other infringements, and to ensure its confidentiality performance, completeness and availability.
- Achieve the requirements of information security responsibility level classification and reduce the threat of information security risks.
- Improve personnel’s awareness of, effectively detect and prevent external attacks, etc.
Quantitative targets were met to report security incidents within one hour, and social engineering drill email opening rates and attachment click rates were lower than 10% and 6%.
Qualitative goals can keep pace with the times, meet hierarchical requirements, and improve information security awareness to detect and prevent external attacks.
Implementation status of information communication system protection benchmarks
Core information system protection mechanism:
■ Establish appropriate backup plans for public services in important areas of the computer room and set up:
- F200 automatic fire extinguishing system
- Dual air conditioner main unit backup operation
- Independent dual-circuit uninterruptible power supply UPS power supply system
- Access card swipe control
- Video surveillance
■ Adopted by our hospital Dual backup (HA),At within tolerable time Services are provided by backup equipment.
■ Collection of important configuration settings files of the information communication system Entity isolation backup, adopting AIX dedicated computer operating environment in the HIS system.
■ Daily Execute core system Data backup:
- A copy of remote backup center (DR side) synchronized backup data
- Another tape backup is at Yongqing Advanced Cancer Medical Center
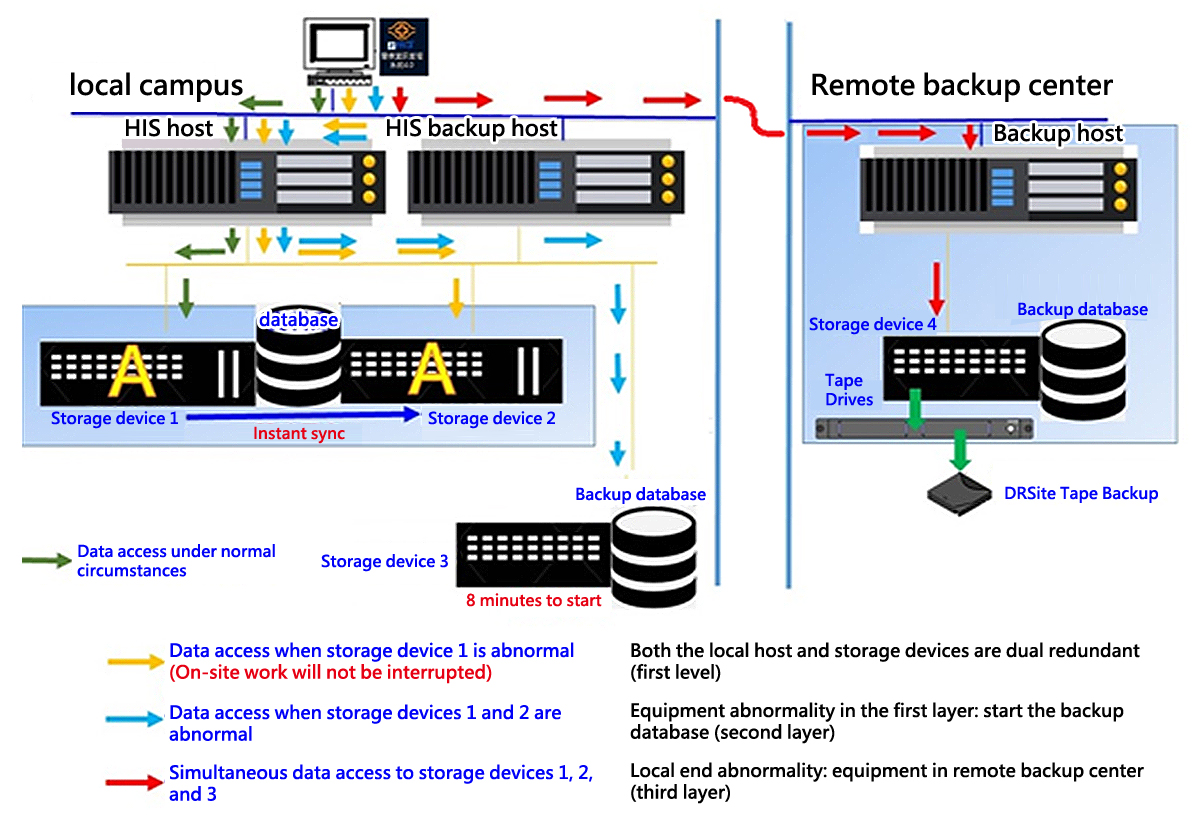
In view of the protection mechanism of the core information and communication system, the computer room is equipped with fire extinguishing equipment, dual air-conditioning hosts, and dual-circuit uninterruptible power supply UPS to ensure the safety of the physical environment of the computer room.
Access control and video surveillance are implemented in the computer room area and office area to strictly control the entry and exit of personnel.
The core systems all adopt high-availability backup, and the backup equipment can take over and provide services within 30 minutes.
Core system data backups are performed daily, one copy is for remote backup, and the other tape backup is stored at Yongqing Advanced Cancer Medical Center.
Implementation status of information security matters to be handled
| Handle projects | Implementation status (detailed description) |
|---|---|
| Information communication system classification | Against 4 core information communication systems complete the information communication system classification, and have completed the control measures for the information communication system protection standards; through project meetings, Review the adequacy of classification at least once a year. |
| Introduction of information security management system and verified by an impartial third party | Information core system from Introduced ISO 27001 verification in 2009, and continue to commission external audits and verifications every year. Complete ISMS internal audits twice a year. |
| Threat detection management mechanism control | The threat detection and management mechanism has been completed. The monitoring scope is as follows: 8 items; The threat detection and management mechanism is entrusted to Guozhong manufacturers and continues to operate and monitor and manage data. Completed monitoring scope: including Anti-virus software, network firewall, email management filtering mechanism, intrusion detection and prevention mechanism (IDS/IPS), application firewall (WAF), advanced persistent threat (APT) defense measures, directory server (AD), Core information system. |
| Information security vulnerability reporting mechanism | Introducing the Information Security Vulnerability Notification Mechanism (VANS) in January 2023, and upload the information assets and installed KBID list of the information security vulnerability reporting system in accordance with regulations. |
| Business continuity operations drills, internal information security audits | Each core information communication system conducts system drills
twice a year. Conduct core business continuous drills once a year. |
| Security testing | Weakness scanning/penetration testing: We have contracts with professional information security vendors to target all core information systems Vulnerability scans 2 times/year,system Penetration testing once per year. |
| Information and communication safety checkup | Information Security and Health Inspection: Contract Entrust professional information security vendors to provide information security and health inspection reports, conduct weakness and vulnerability analysis and improvement based on network architecture, network malicious activities, user computers, malicious activities, server host malicious activities, directory server settings and firewall connection settings review. |
| Information Security Threat Detection and Management Mechanism | Imported in February 2023 (SOC), the collected data is being processed one after another. |
| Information security protection | Anti-virus software: Trend Micro anti-virus software is installed on all HIS computers in the hospital, and updates and virus attack status are monitored daily. Update anti-virus software regularly. |
| Network firewall: Check the source IP address, destination IP address, source/destination PORT of each packet, Filter illegal connection packets, and provide auditing and control access to network resource services. | |
| Email filtering mechanism: The content and classification of emails will be filtered before being sent to the hospital to block abnormal emails, to ensure the security of receiving mail. | |
| Intrusion detection and prevention mechanisms: Features Sourcefire IPS with daily updated characteristic values, deep packet inspection blocks known types of attacks and zero-day vulnerability attacks. | |
| Application Firewall: Application firewall set up to protect against common attacks on web applications. | |
| Advanced Persistent Threat: Attack Defense APT defense server has been established, providing advanced persistent threat attack defense services for Internet and email. |
Our hospital is a Grade A critical infrastructure hospital, and all listed tasks have been implemented and met the requirements.
Information security protection system
Guided by patient privacy, a multi-channel information security protection system is constructed to prevent virus intrusions, illegal connections, phishing or malicious website control (social drills), as well as virus and Trojan protection, regular vulnerability scanning, etc. The detailed structure is as follows:
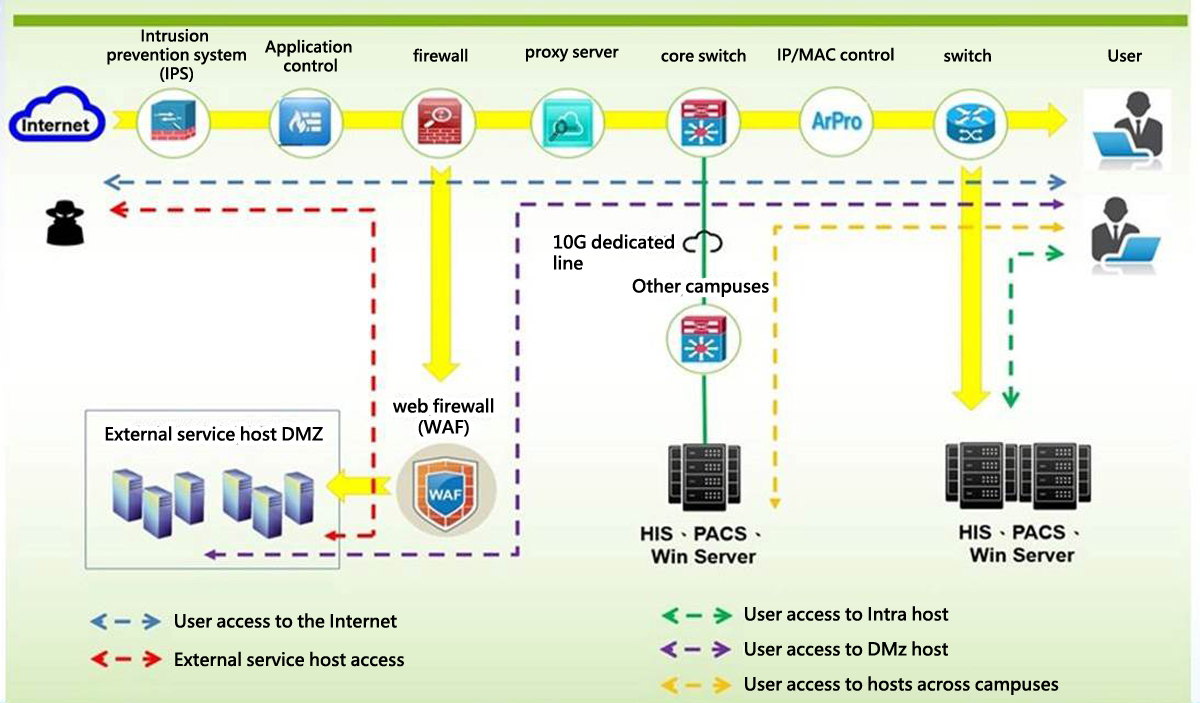
Information security control
◎ Obtained the ISO information security management system certification for the first time on April 15, 2009, and officially obtained the TAF (domestic CNS 27001:2006) and UKAS (foreign ISO 27001:2005) licenses on May 19
◎ Obtained the fifth 3-year follow-up certification update (ISO 27001:2013) on May 24, 2021, and conducted ISO 27001:2022 transition update verification on April 10, 2024.




Information security education and training
| Personnel category | Training content | Hours required | Number of people and units involved |
|---|---|---|---|
| Information security dedicated staff |
Information security Professional course training Or information security functional training |
Each person receives at least twelve hours per year | 4 people (computer class) |
| Information security Other than dedicated personnel information personnel |
Each person must receive at least three hours of training every two years | 11 people (computer class) | |
| Information security General education training |
Each person receives more than three hours per year | ||
| General users and supervisors |
Each person receives more than three hours per year | 6,247 people (All departments of the hospital) |
|
| Total | 6,262 people | ||
As for information security education and training, the four dedicated information security personnel have completed more than 12 hours of professional or functional training every year in compliance with regulations; the remaining staff have received more than 3 hours of general education training every year. The table on the right shows the three information security general education sessions conducted last year. Course completion rate has reached 99%.

